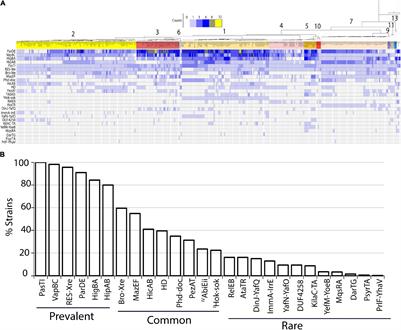
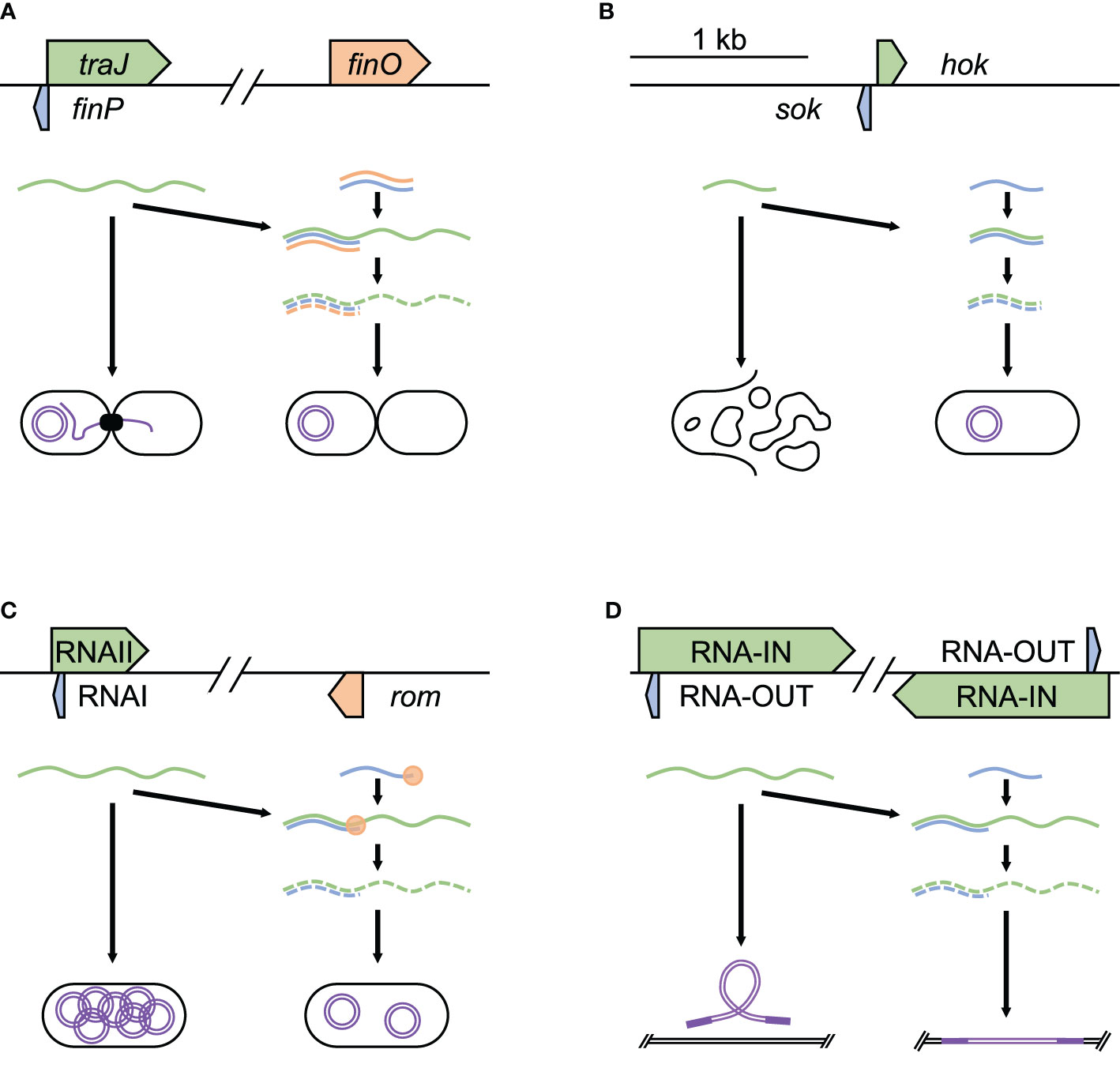
Frontiers | Genome Mining Shows Ubiquitous Presence and Extensive Diversity of Toxin-Antitoxin Systems in Pseudomonas syringae
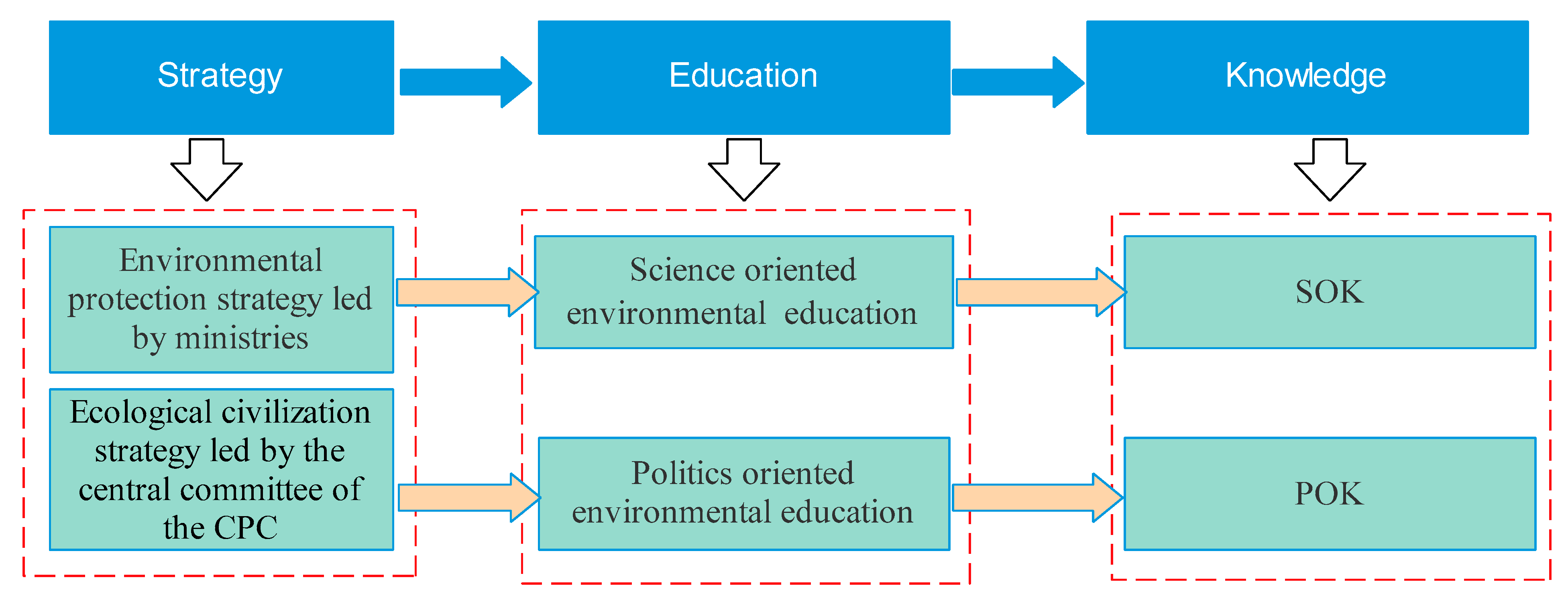
Sustainability | Free Full-Text | Differentiated Impact of Politics- and Science-Oriented Education on Pro-Environmental Behavior: A Case Study of Chinese University Students
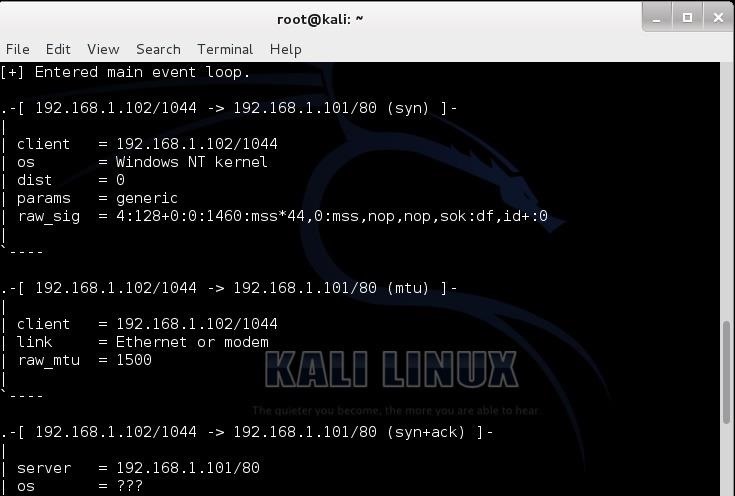
Hack Like a Pro: How to Use the New p0f 3.0 for OS Fingerprinting & Forensics « Null Byte :: WonderHowTo
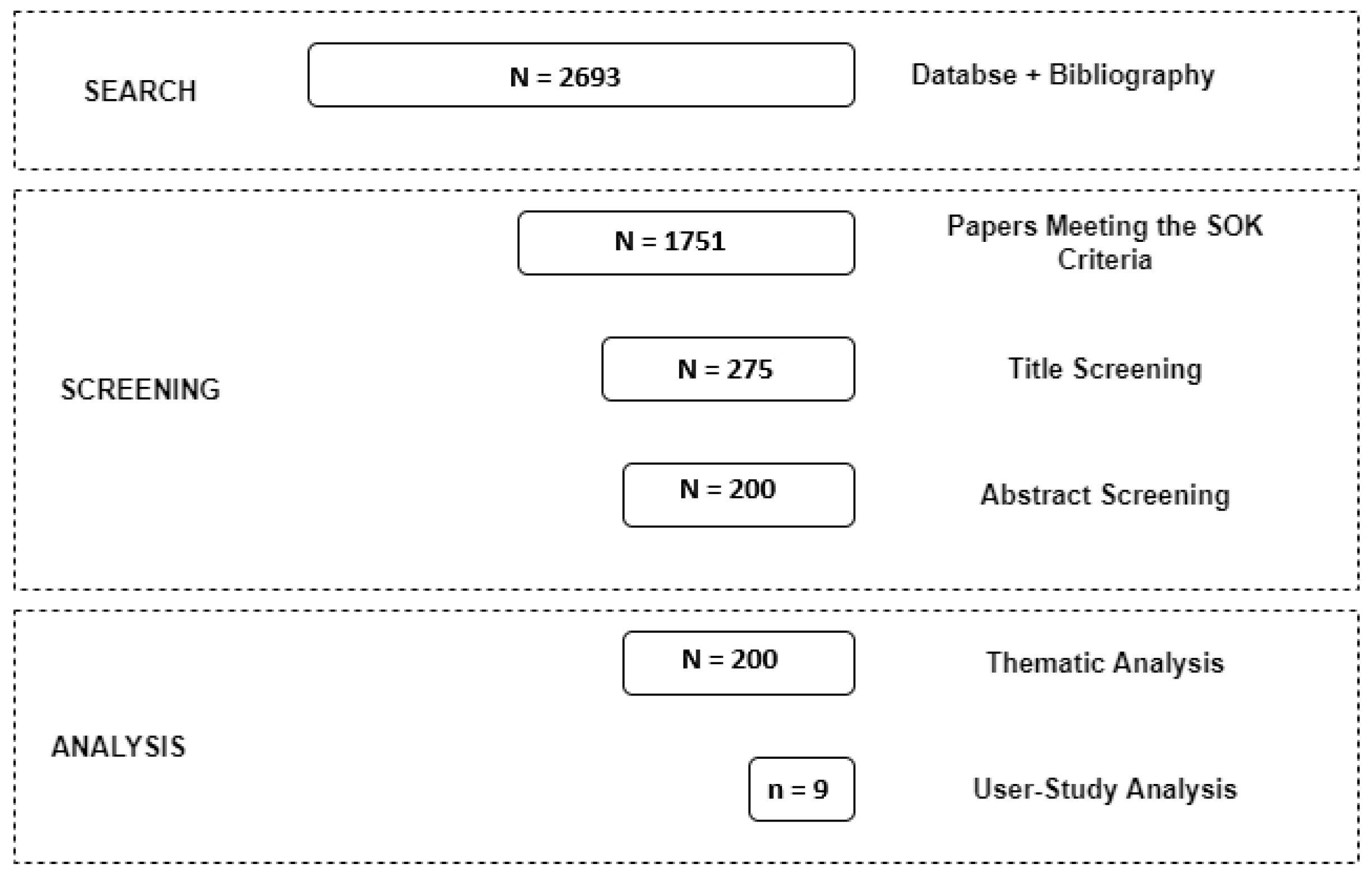
JCP | Free Full-Text | SoK: An Evaluation of the Secure End User Experience on the Dark Net through Systematic Literature Review
![PDF] SoK: P2PWNED - Modeling and Evaluating the Resilience of Peer-to-Peer Botnets | Semantic Scholar PDF] SoK: P2PWNED - Modeling and Evaluating the Resilience of Peer-to-Peer Botnets | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6e1ed432822ea31fd2d83cf273fdae646ac890ec/10-Figure4-1.png)










![PDF] SoK: Applying Machine Learning in Security - A Survey | Semantic Scholar PDF] SoK: Applying Machine Learning in Security - A Survey | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a3f147f808ec58f5e9aeb4124fb90cd9bc034672/9-Table4-1.png)