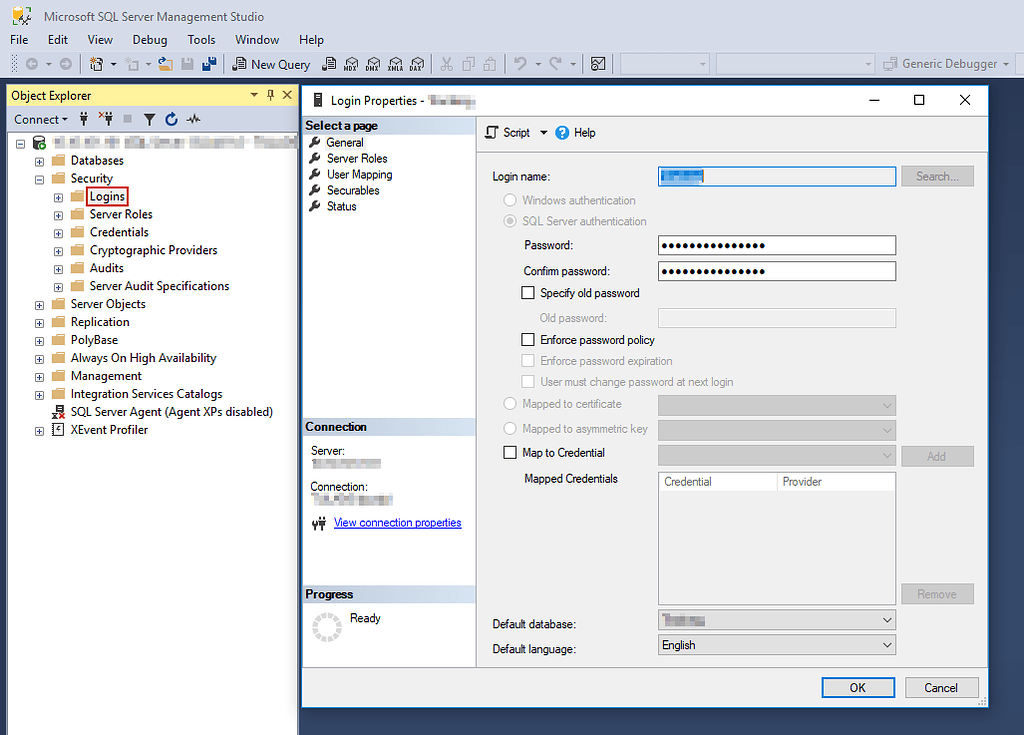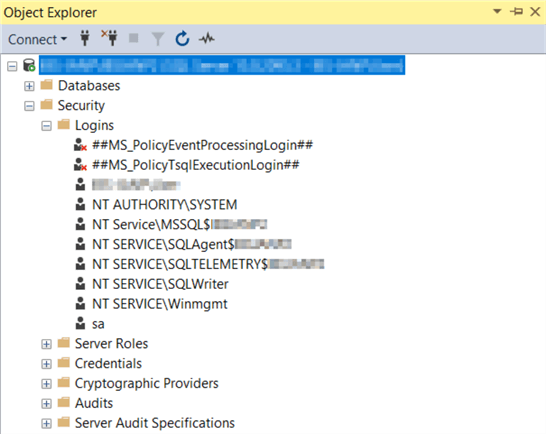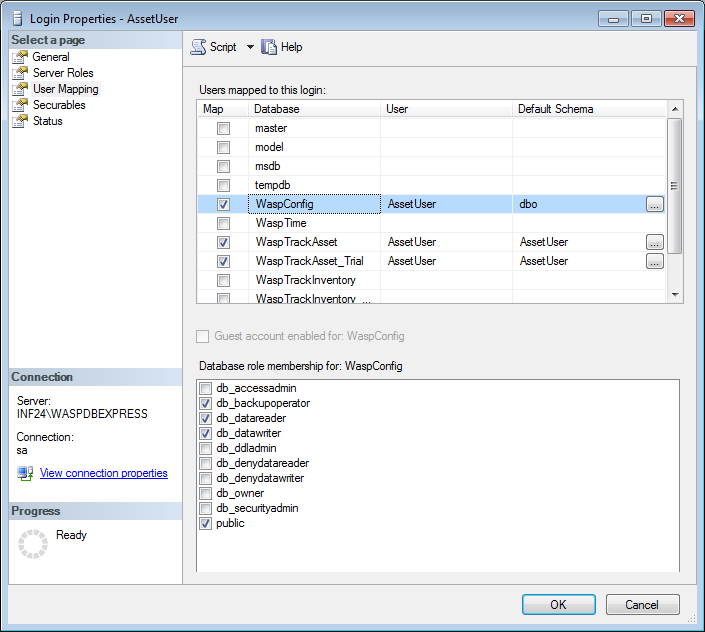
SQL Server User Mapping for InventoryControl, MobileAsset, WaspTime - Knowledgebase / Discontinued Products / MobileAsset / Version 7 - Wasp Helpdesk

SQL Server 2019 Users and Security |SQL Server 2019: Security with Users, Schemas, and Roles - YouTube

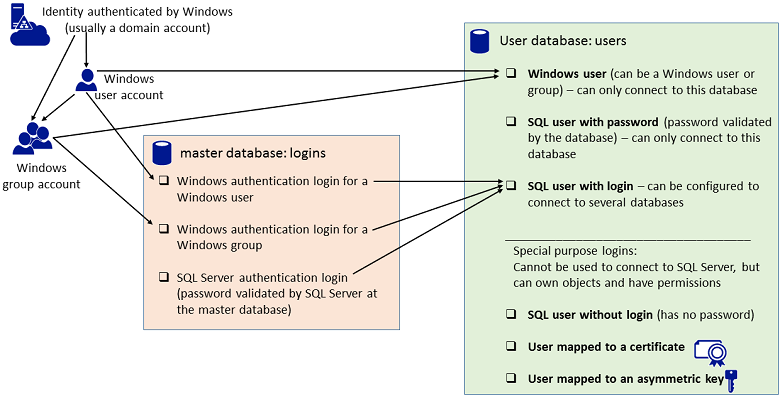
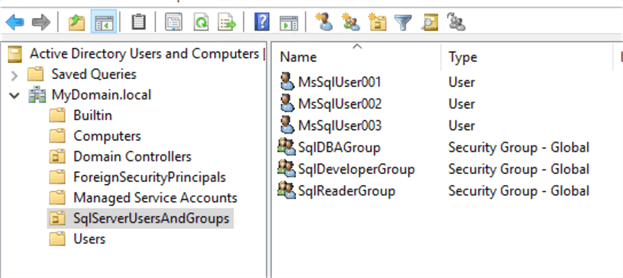
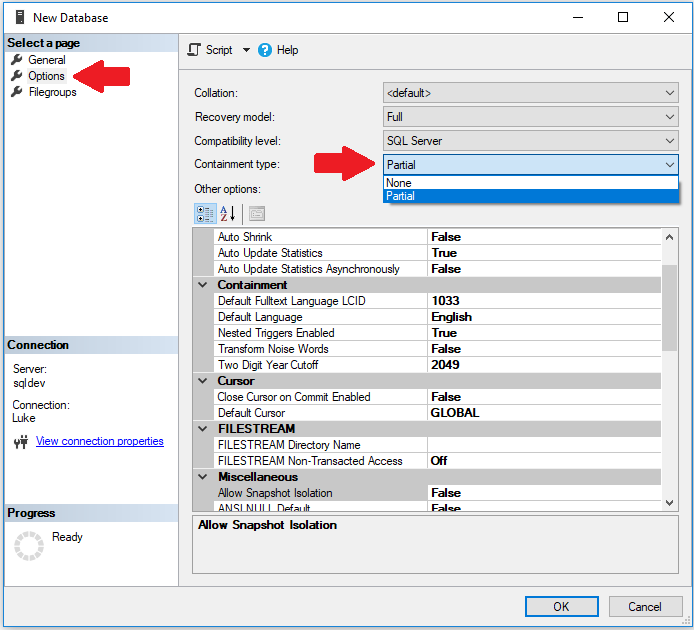
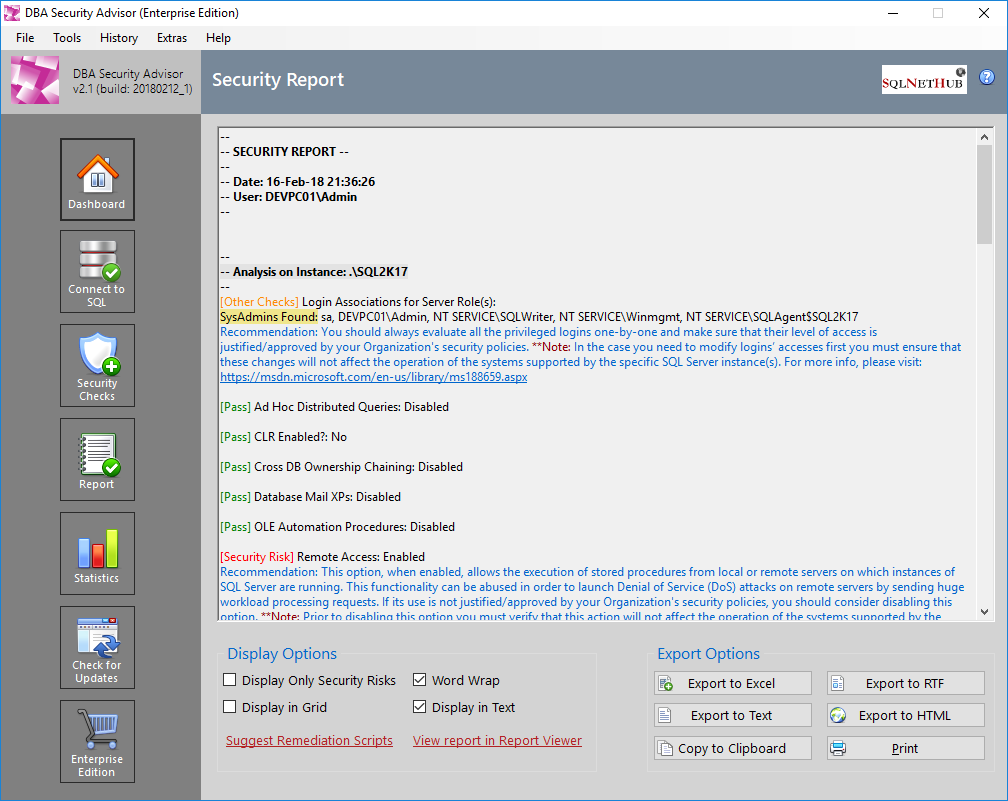
SQL Server Users Explained: Back To Basics - TechNet Articles - United States (English) - TechNet Wiki